 A
A
longer term project is to get the web-server lievenlb.local integrated in our home-network
as an external WebDAV-server (similar to the .Mac-service
offered by Apple). But as this server runs all information about the
master-class on non-comutative geometry connecting to it via HTTP to use
WebDAV is too great of a security risk as all username/password
combinations will be send without encryption. Hence the natural question
whether this server can be set up to run SSL (Secure Sockets
Layer) such that one can connect via HTTPS and all exchanged information
will be encrypted. As the server is an Apache it comes down to get
mod-ssl running. A Google on mod_ssl OS X gives the
ADC-document Using mod-ssl on Mac OS X which seems to be just
what I want. This page is very well documented giving detailed
instructions of using the openssl command. However, the
end-result is rather weak : it only makes the localhost running
HTTPS, that is, one can connect to your own computer safely… which is
pretty ridiculous (other computers in the same network cannot even
connect safely).
So, back to the Google-list on which
one link raises my interest Configuring mod-ssl on Mac OS X which looks like
the previous link but has one essential difference : the page is written
by Marc Liyanage. If you ever tried to get PHP and/or MySQL
running under OS X you will have noticed that his pages are by far the
most reliable on the subject, hence maybe he has also something
interesting to say on mod-ssl. However, the bottom line of the
document is not very promising :
You
should now be able to access the content with https://127.0.0.1 from
the same machine.
which is again the
localhost. So perhaps it is just impossible to run mod-ssl
without having an X-server. Anyway, let us try out his procedure.
Begin by issuing the following commands in the Terminal
sudo -s cd /etc/httpd mkdir ssl chmod 700 ssl cd ssl gzip -c --best /var/log/system.log > random.dat openssl rand -rand file:random.dat 0
Next, we need a server certificate. If you
want to do it properly you need a certificate from a certification
authority such as Thawte but this costs at least $200 a year which I
am not willing to pay. The alternative is to use a self-signed
certificate which will force the browser to display an error-message
but if the user dismisses it all traffic exchanged with the server will
still be encrypted which is just what I want. So, type the command
openssl req -keyout privkey-2001.pem -newkey rsa:1024 -nodes -x509 -days 365 -out cert-2001.pem
(all on one line).
You will be asked a couple of questions (the only important one is the
Common Name (eg, YOUR name). Here you should take care to enter
the host name of your web server exactly as it will be used later in the
common name field. In my test-case, if I want to get my server
used by other computers in the network this name will be
imaclieven.local. (note the trailing .). Now issue the following
commands
chmod 600 privkey-2001.pem chown root privkey-2001.pem apxs -e -a -n ssl /usr/libexec/httpd/libssl.so
which will activate the SSL-module (if at a later state you want
to de-activate it you have to change -a by -A in the last command).
Finally, we have to change the /etc/httpd/httpd.conf file so
first save a backup-version and then add the following lines at the end
of the file :
(IfModule mod-ssl.c) Listen 80 Listen 443 SSLCertificateFile /etc/httpd/ssl/cert-2001.pem SSLCertificateKeyFile /etc/httpd/ssl/privkey-2001.pem SSLRandomSeed startup builtin SSLRandomSeed connect builtin (VirtualHost -default- :443) SSLEngine on (/VirtualHost) (/IfModule)
Observe that round brackets ()
should be replaced by <>. Finally, we do
apachectl stop apachectl start
and we are done! Going to another computer
in the network and typing in Safari https://imaclieven.local./
will result in an error message
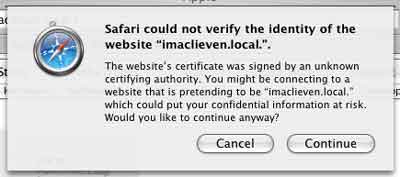
Just click Continue and you will have a secure connection
to the server. Thanks Marc Liyanage!
(Added january
11th) Whereas the above allows one to make a HTTPS connection it is not
enough for my intended purposes. In order to get a secure connection to
a WebDAV server, this server must have the mod-auth-digest module
running which seems to be impossible for the standard Apache server of
10.3. You need an X-server to have this facility. So I think I have to
scale down my ambitions a bit.
 We
We